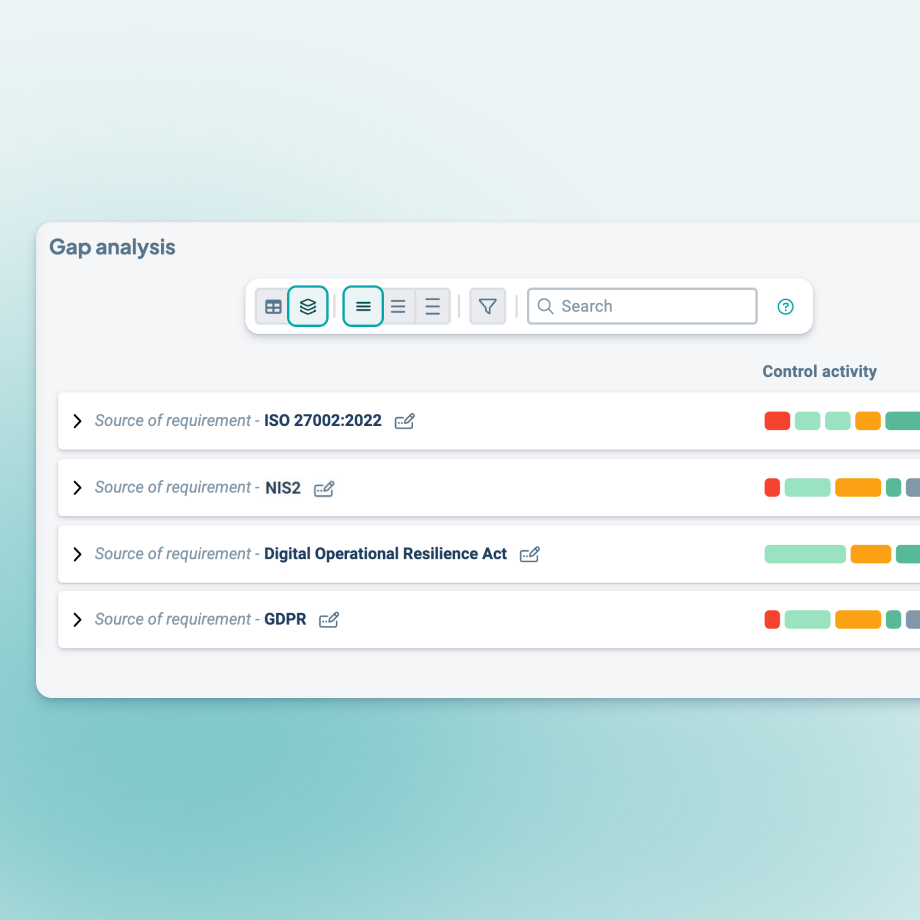
Improved overview of current situation
Do you find it difficult to get a clear overview of how your organization meets DORA? With the help of Stratsys, you can develop a baseline analysis to identify differences in your current state and desired target state. This will give you insights into what needs to be done to comply with DORA.

.png?width=690&height=690&name=dora%20(1).png)






%20(1).png?width=600&height=600&name=imaginestratsys_a_woman_standing_outside_an_office_builing_ente_68b8e2c9-0420-480c-81bd-564fe7a586c2%20(2)%20(1).png)